In today's world Tor browser is an amazing system to hide the identity of the user and browse safely all the world around. This is a free system and an open software where internet traffic is totally free and used thoroughly anytime & anywhere can browse without marking the identification of the user. Hardly can trace the user address and location while using Tor Browser. So it is safe and ensures the highest level of safeness for sending messages or visiting different websites through Tor browser. On the contrary, some people think that Tor can be used for different illegal jobs or purposes and cyber crimes. But this thinking is not so strong to prove the illegality of using this browser. Rather Tor has some strict issues to prevent illegal works and make safe uses for the betterment of the world. The dark web side is the most strong tool to maintain the safety of its users and increase anonymity. So Tor browser is not harmful for the mass people or its not involved with the odd, criminal or any cyber crime activity. But some websites do not accept the IP from Tor Browser. Because they need the users identifications and the traffic area of their users. This time the sites may block the identity or the ip of throes users. So it needs to be more careful to browse in the right way. Though Tor provides a hard security system, some people can mark the identification of Tor anonym users. Though it has a powerful protocol and strong activity in anonymity of users, sometimes it takes huge time to load a data or file transferring, because its working system is a little bit slow when it faces the problem of accessibility in many sites.
Read More : Different Types of Messenger Tricks and Topics
This browser has the most powerful system from its launching time. The official date of its launching is 20 September, 2002. From that time Tor Browser was made for the Naval Research of the USA. After that it increased its data encryption system as a layer based software like an onion. For that cause the project was named after The Onion project.
How to Download Tor browser :
Downloading the Tor browser was not so difficult. This browser is available for all the terms and conditions in any windows pc, Linux, iOS or for the android devices one can download tor in the plays tore from this Link :
For android : “Download Tor Browser for Android “
For PC: “Download Tor Browser for Windows PC ”
Or from The Official Project :
Download Tor Browser
Or one can download this manually from different websites as they need the versions variations. These websites also provide a lot of links to download or update this browser.
Introducing with Tor homepage :
After downloading and installing the browser everyone can see the inserted image About Tor. This is the main browsing page or the homepage of Tor browser. If you want, you can make a search from this page with the “DuckDuckGo” or the normally Tor search option. You can find all the active sites from there. But it is more safe to search by Tor site. The rank between the Tor and DuckDuckGo is respectively 3rd and 6th. So Tor is the best searcher than DuckDuckGo.
Manual Tor Browser :
In the homepage there is an option for tor manual browse. Here you can see the website of Tor and by dragging down you can get the options for downloading the browser. Click there and you will get the option to download the browser for every sector like Windows or Mac etc.
For downloading windows : “Download Here “
For downloading Mac or iOS : “Download Here “
For downloading Linux : “Download Here “
For downloading Android : “Download Here “
For the Mobile Phone Users :
A huge number of people are using Tor browser everyday with their mobile phone. Making an easy Tor browser in mobile phone use the Tor project Authority gives us the option to use their browser into the phone.
Download Tor Browser for Android
Users of Tor Browser :
Generally the mass people of the local area who are concerned about their security and maintaining the privacy of the location are the main users of this browser. But it has the hardest security system that different types of intelligence departments use this browser for control the system of the country and find out the crimes of the area. Again this site is used in the military or the investigational works which are done for the betterment of the nation or the country. The Naval Security Force is the main follower of this browser from the era of its starting. Actually for the unique feature of this browser like the anonymity and the hiding location of the user, it gets the first priority to the professional workers like the IT professional or the Technologists.
Dark side :
To describe the dark side, at first we need to know what is the dark side? And what is the darknet ? actually both of them are similar in meaning. Dark side or the dark net are generally used for the underworld related terms and policies where all types of odd deeds and deals are occurred. These jobs are in the world wide system. But for these occurrences every area needs to become connected with each other. In this era of the internet this is not a big deal to contact each other. But doing these dark jobs openly is not available, for this its need to hide the real identity but dealing with others. Some specific software is used to do this type of work. Tor Browser is the system software of these dark websites. Tor web has been designed as a software where IP addresses and protocols cannot be shown, rather the identity of the users are in secret that can hardly be found. It has a secret system to identify its own customers by their domain name only. The domain is “.onion” . But it cannot be able to identify the real identity of a man.
In the dark side business all the types of illegal deals such as illegal drug exchanging, slaves buying and selling, illegal weapons and others marketing, exclusive and attractive media board exchanging etc. have occurred regularly. Some dark side browsers are :
1.anoNet is a software where a friend-to-friend network is built by using VPN and other software BGP routers works.
2.BitTorrent is a unique and high transmitted software where semi-decentralized and peer-to-peer communication is done by the protocol.
3.Decentralized network 42 does not for anonymity of person but using for research purposes.
4.Freenet is one of the most DHT files serving the darknet platform in this era. It supports the friend-to-friend and open net modes only.
5.GNUnet can be used for browsing a darknet if the F2F (network) topology option is enabled there.
6.I2P (Invisible Internet Project) is an overlay proxy network that features cannot be seen in public but also services its users highly is called "Eepsites".
7.IPFS has a browser extension which can be used to backup popular web pages for browsing.
8.OpenBazaar is an open source software developing system and a protocol for e-commerce transactions. In this marketplace all types are fully decentralized by the security system.
9.RetroShare is an alternative messenger communication and file transfer platform for the dark side business. It may be sometimes used as a darknet if DHT.
10.Riffle is a government and client-server darknet system that provides secure anonymity in together, efficient computation, and minimal bandwidth burden.
11.Secure Scuttlebutt is a system of peer-to-peer communication technology, mesh networking system and self-hosted social media.
12.Syndie is a software which works for publishing distributed forums over the anonymous networks like I2P, Tor and Freenet.
13.Tor (The onion router) is an anonymity network that also works as a darknet side via its onion project.
14.Tribler is an anonymous BitTorrent client which is built as a search engine.
15.Zeronet is a DHT Web based 2.0 hosting software which is related to Tor browser.
ABOUT BROWSER FUNCTION :
Operating the system of this browser is so user friendly that everyone can use this browser very easily. The most important feature of this browser is its security system and the other
Tor Security Levels :
Tor security levels play one of the most important parts of browsing data of all the browsers because different levels are used for different tasks. Their main activity plays the vital role for visiting different types of websites browsing and so on. It seems to be the control of the Tor also. Mainly the browsing system of Tor partially depends on this setting. Now let's have a discussion about the security and its activities.
1. Standard (default) security system : This is the security system in which all the browsers features are enabled to work properly. This security system has not the hardest level of data encryption system or not provides the highest level of security system.
2. Safer : in this security system some of the changes can be noticed. Some websites lose their activity and may be cause for disablement of the site. It causes the limitation of the specific websites. Some of the features are-
i) JavaScript is not enabled on non-HTTPS sites.
ii) On sites where JavaScript is not disabled, performance optimizations are not enabled. Scripts on some sites may run slower.
iii) Some mechanisms of displaying math equations are disabled.
iv) Audio and video (HTML5 media), and WebGL are click-to-play.
3. Safest : Only allow websites to be used at this security level. The regulation of the images or videos or articles can be affected by this security system. Another some problems are-
i) JavaScript is disabled by default on all sites.
ii) Some fonts, icons, math symbols, and images are disabled.
iii) Audio and video (HTML5 media), and WebGL are click-to-play.
New Identity :
New identity is to reset all the data, system, tabs, browsing history genuinely clear all the sessions in a tap. Rather your identity is also removed to this session also. Actually this feature is to use as a short-cut way to clean the Tor browser properly.
Download Tor Browser
Library :
Library is the option where the browsing history, downloads and bookmarks files are found. If someone loses his browsing data, he can check his browsing history and bring back his datum again.
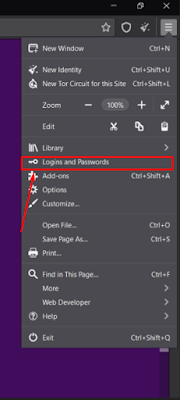
Login & Password :
Tor browser has the options to save your passwords for the future use. For this option you no need to save your passwords more and more times. Even if you forget your password by any chance, you can check the password from that saving options page.
Ads-on :
Advertisement and Discovery of Services is one kind of important feature for maintaining the extensions and the ad blocks. Tor is mainly used for the purpose of ensuring the system of security is safer than the other browser has. As they do not block the ads but show them so you have a question to the safety of yours. For avoiding this situation tor provides its users the ads-on method where they can browse without any risk. Tor also offers us the plugin method to browse more smoothly.
Themes :
To make Tor eye friendly tor offers us different themes which make them beautiful too. You can enjoy themes from the Ads-on option.
Download Tor Browser
Options :
To Control the system there needs for the options where one can personalize his systems as he looks for. in Option one will get all the features at a time he needs.
Customize :
One can change the system and the icon bars by dragging left to right or right to left.
Others :
Without these Tor also has some other information to make this browser user friendly and helpful. Tor has the options to open any file in that browser and search finder to search a specific item. Help option to get any kind of help at the time of trouble or anything else. If you need to print any documents, just tap on the print and your file will be ready to print out.
Actually tor is a browser where all types of works can be done. It is needed to make the world easier, another side it can bring the curse for the human being also. It's totally up to you which types of works you need to do. Man has the conscious mind and also a creative brain by which a man can do anything he wants for. So we should use the right use of our technology for the betterment of our own. Rather will make ourselves ruined.




















Post a Comment